A review of a Sybil attack in wireless sensor networks
In no more than 2000 words, write a literature review on Sybil attack in wireless sensor networks. All references must be consistent with the IEEE referencing style.
Introduction: The increased growth in wireless sensor networks (WSNs) in both civilian and military communities has attracted wide attention [1-3]. Much of the attention has to do with improving the technology and enhancing the efficiency and efficacy of WSNs; however some of the attention is rather dubious and has to do with problems that have trailed the emergence of WSNs. One of these is the attack intentionally created to defraud the network. In wireless sensor networks (WSNs), a single node, called a faulty entity [4], can generate multiple identities in order to gain illegal access into the network. The essence of generating multiple identities is that many nodes are presented to trick the relevant legitimate nodes; the network can be penetrated to allow an attack such as service denial [5]. Such multiple identities from the malicious node that are presented as multiple nodes are described as Sybil nodes. If such an attack is successful, it can be characterised as a Sybil attack [4, 6] which has been identified as a serious problem in the design of sensor networks [7]. It is possible to mitigate the attack in WSNs, for static nodes but designing sensor network nodes that pre-empt this problem for mobile Sybil nodes has yet to be developed. Figure 1 represents a typical Sybil attack phenomenon where an attacker is disguised as different nodes.
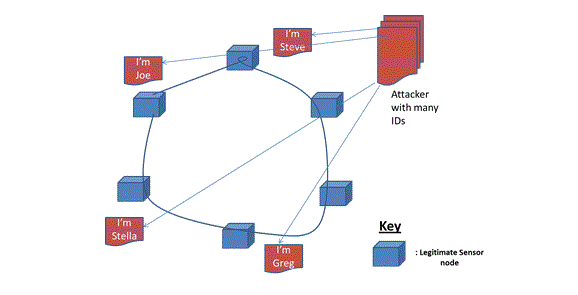
Figure 1: Wireless Sensor Network showing Sybil Attacker with many IDs
To one node, the Sybil node is Steve but to another, it behaves as Joe, Stella, Greg, etc. Any of the nodes which the attacker successfully confuses may trust the malicious node as being a legitimate node.
Methods of Sybil Attack: Sybil attack operations can be grouped into three methods, namely: direct and indirect communication with the legitimate nodes, fabricated and stolen identity, and simultaneity attacks [8]. In direct communication, a Sybil node sends a message directly to the legitimate sensor node while one of the Sybil nodes listens. In indirect communication, one of the Sybil nodes pretends to communicate directly with the Sybil node while the Sybil node routes the message through one of the illegitimate nodes. In the second case, identity (ID) can be fabricated by creating, arbitrarily, new Sybil nodes or nodes stolen from the legitimate nodes by way of impersonation. In simultaneity and non-simultaneity operations, an attacker either presents all her identities at once or presents them in batches respectively.
Types of Sybil Attacks: If access can be gained to the network using any of the above-mentioned methods, the Sybil attacker can perform its operation in any of the following ways [8]:
a) Distributed Storage: In a peer-to-peer network, IDs are fragmented and stored in a sink or nodes. If a Sybil attack obtains access to the network, the fragmented or replicated IDs can be unwittingly stored in a malicious node [4]. As a corollary, this is the major problem in other security techniques that involve fragmentation of IDs and storing them in a sink or different admin nodes. For instance, to secure fragmented keys, they are fragmented into RSAs so that they can be reconstructed. In wider area networks, the storage nodes may be located at different geographical coordinates. If a Sybil attack succeeds, this defeats the idea of distributed geographical hash tables as in [9-11].
b) Routing: Multipath routing and different geographical routings are ways of performing routing [8, 12]. Since a Sybil attacker generates multiple nodes, it is possible that for all different multipath routings or different geographical routes, some Sybil nodes exist.
c) Data Aggregation: To conserve energy, some efficient sensor network protocols aggregate each sensor reading instead of returning different individual readings [13]. These readings can be mutilated by a Sybil node.
d) Voting: WSNs nodes can vote, for instance, to determine an attacking node. If a Sybil attacker penetrates a network with IDs well enough, it is possible to vote out a legitimate node or blackmail a legitimate node.
e) Fair Resource Allocation: It is possible that if a Sybil node penetrates a network, such as during resource sharing, an attacker can obtain unfair network resources.
f) Misbehaviour Detection: Sybil nodes can accuse legitimate nodes of misbehaving. In this case, if votes are to be cast (with the Sybil node having more IDs), legal nodes can be detected as misbehaving nodes.
Mitigation Techniques: Approaches to block attacks are growing as fast as the attacks are growing [7]. Security paradigms include preparing to intercept these attacks even before they are invented [14, 15]. Some of the known mitigation methods presented against Sybil attacks promise an appreciable likelihood of tracking down malicious attempts with up to 99.8 per cent reliability [2]; others indicate 100 per cent reliability [6]. Some methods have proposed the use of symmetric cryptographic keys [12]. Below, well-established detection algorithms are reviewed. These techniques have demonstrated the inclusion of the radio resource testing (RRT) method, the received signal strength indicator (RSSI) method, and the positioning, voting, two-level Merkle hash tree method [4, 16], etc.
a) RRT: In radio resource testing, it is assumed that a physical device cannot transmit along more than one channel. Since the radio channel is assumed to be the same for any node, a Sybil attacker will always transmit on the same radio channel with multiple IDs [8]. The problem with this technique is that it is wasteful to transmit on different channels for each node. For instance, multicarrier transmissions may not be possible except for single transmissions.
b) RSSI: In addition to verifying IDs, the RSSI mitigation technique computes the time difference of arrival (TDOA) of a verifying ID message and predicts the location of the transmitting node. Sybil nodes will always come from a single node pretending to be many nodes with the same signal strength and location. Because traditional RSSI is time-varying, lacks dependability and its radio transmission is non-isotropic, this scheme fails [17]. However, when the ratios of the RSSIs are observed, experiments have shown up to 100 per cent mitigation [6]. The disadvantage is that calculating the locations is computationally expensive.
c) Positioning: This method verifies the position of a node. Sybil nodes will always be in the same position. This method fails for non-static nodes. It has been proposed [18] that a cooperative RSS-based Sybil detection (CRSD) technique can be used; this involves cooperative information from legal nodes. The combined radio resource and ID of the node is used to detect Sybil attacks. This method is limited to a stationary attacker and does not account for more than one malicious node.
d) Registration: In some WSNs, one node may be established that would be trusted by all other nodes. In this case, all nodes verify each other node’s ID here.
e) Neighbour Identification: By the neighbour discovery method, a data structure is built for the first hop with which malicious nodes are detected and isolated. Neighbours exchange identities with individual commitment keys for mutual authentication. To ensure there is no compromise, commitment keys expire at some stage. Just before expiration, the last set of the previous commitment keys are used to generate another set of undisclosed commitment keys with the one-hop source authentication protocol. The one-hop source authentication protocol helps a node to identify its neighbour. This could be bewitched by an attacker if it blocks the transmission range [3]. Other detection techniques involving neighbouring information have been discussed in [2].
f) Neighbour Number Test: The use of a neighbour number test (NNT) and the all distance test (ADT) was proposed in [3]. The NNT calculates the number of neighbouring nodes whereas ADT computes the proximity of those neighbours. The results of many neighbouring nodes could be used to identify a Sybil attempt. Others consider the mutual interaction between nodes [2]. This idea uses neighbouring information; malicious node-generating multiple identities can be tracked down. The danger of this method is that some legitimate nodes can be denied access at some points [8]; others can be mistaken for malicious nodes in the event of the central authenticating node’s failure[4]. The experts have not been able to show how Sybil attacks can be mitigated in cases where the generating (malicious) node is not stationary or there are more than one.
Each of the methods discussed have advantages with their respective overheads. All of these methods report the condition of stationary Sybil attacking nodes. Though it has not been reported that malicious nodes attempting attack were by a non-stationary approach, it could have been a way by which most of the Sybil attack operations have/will successfully been/be carried out.
Conclusion: A Sybil attack pollutes a wireless sensor network. It defrauds the legitimate nodes by replicating itself as many different nodes. Several ideas have been proposed to mitigate the attack but available mitigating techniques have not dealt with cases where the Sybil nodes are mobile. Consequently, techniques for mitigating Sybil attacks of mobile Sybil nodes can avoid many dangers in sensor networks.
Reference
[1] Q. Zhang, P. Wang, D. S. Reeves, and P. Ning, “Defending against sybil attacks in sensor networks,” in 25th IEEE International Conference on Distributed Computing Systems Workshops, 2005. 2005, pp. 185-191.
[2] K.-F. Ssu, W.-T. Wang, and W.-C. Chang, “Detecting Sybil attacks in Wireless Sensor Networks using neighboring information,” Computer Networks, vol. 53, pp. 3042-3056, 2009.
[3] I. Khalil, S. Bagchi, C. N. Rotaru, and N. B. Shroff, “UnMask: Utilizing neighbor monitoring for attack mitigation in multihop wireless sensor networks,” Ad hoc networks, vol. 8, pp. 148-164, 2010.
[4] J. R. Douceur, “The sybil attack,” in Peer-to-peer Systems, ed: Springer, 2002, pp. 251-260.
[5] R. Muraleedharan, Y. Yan, and L. A. Osadciw, “Detecting sybil attacks in image senor network using cognitive intelligence,” in Proceedings of the First ACM workshop on Sensor and actor networks, 2007, pp. 59-60.
[6] M. Demirbas and Y. Song, “An RSSI-based scheme for sybil attack detection in wireless sensor networks,” in Proceedings of the 2006 International Symposium on on World of Wireless, Mobile and Multimedia Networks, 2006, pp. 564-570.
[7] B. N. Levine, C. Shields, and N. B. Margolin, “A survey of solutions to the sybil attack,” University of Massachusetts Amherst, Amherst, MA, 2006.
[8] J. Newsome, E. Shi, D. Song, and A. Perrig, “The sybil attack in sensor networks: analysis & defenses,” in Proceedings of the 3rd international symposium on Information processing in sensor networks, 2004, pp. 259-268.
[9] S. Ratnasamy, B. Karp, L. Yin, F. Yu, D. Estrin, R. Govindan, and S. Shenker, “GHT: a geographic hash table for data-centric storage,” in Proceedings of the 1st ACM international workshop on Wireless sensor networks and applications, 2002, pp. 78-87.
[10] S. Shenker, S. Ratnasamy, B. Karp, R. Govindan, and D. Estrin, “Data-centric storage in sensornets,” ACM SIGCOMM Computer Communication Review, vol. 33, pp. 137-142, 2003.
[11] S. Ratnasamy, B. Karp, S. Shenker, D. Estrin, R. Govindan, L. Yin, and F. Yu, “Data-centric storage in sensornets with GHT, a geographic hash table,” Mobile networks and applications, vol. 8, pp. 427-442, 2003.
[12] C. Karlof and D. Wagner, “Secure routing in wireless sensor networks: Attacks and countermeasures,” Ad hoc networks, vol. 1, pp. 293-315, 2003.
[13] S. Madden, M. J. Franklin, J. M. Hellerstein, and W. Hong, “TAG: A tiny aggregation service for ad-hoc sensor networks,” ACM SIGOPS Operating Systems Review, vol. 36, pp. 131-146, 2002.
[14] D. Gollmann, Computer Security, 3rd ed.: Wiley, 2011.
[15] R. Panko, Corporate Computer and Network Security, 2/e: Pearson Education India, 2004.
[16] J. Yin and S. K. Madria, “Sybil attack detection in a hierarchical sensor network,” in Third International Conference on Security and Privacy in Communications Networks and the Workshops, 2007. SecureComm 2007. 2007, pp. 494-503.
[17] D. Kotz, C. Newport, R. S. Gray, J. Liu, Y. Yuan, and C. Elliott, “Experimental evaluation of wireless simulation assumptions,” in Proceedings of the 7th ACM international symposium on Modeling, analysis and simulation of wireless and mobile systems, 2004, pp. 78-82.
[18] S. Lv, X. Wang, X. Zhao, and X. Zhou, “Detecting the sybil attack cooperatively in wireless sensor networks,” in International Conference on Computational Intelligence and Security, 2008. CIS’08. 2008, pp. 442-446.