Essay on Attribute Based Encryption Using ESP32 Platform
Number of words: 3431
Abstract— IoT is also known as things connected with the internet. In this, people control their things by internet. Though it has huge advancement as it connected with internet, there has lot of privacy and security concerns. It can be affected by viruses, malware, spam ware, etc. It can be hacked easily. Privacy concerns are also there. It will store the data, personal information, identity of the owner which will become vulnerable. From this information, people can be affected physically also. But some of this problem can be minimized and some of this can be eliminated using various techniques. If the systems encrypt then the hacking problem would be less. Using antimalware, antivirus, etc. it would be safer. Using Artificial Intelligence can be more effective. The company should use fewer data of the owner and the data protection system should be stronger. Making strong firewall can resolve the security issues. The developers of IoT should care about the less power consumption of the system Proper planning is essential for the launch of IoT devices. The developers should be aware of the latest threats of security so that they can overcome them. The system should be timely maintained and updated. Data safety is the key concern for the privacy and security of IoT. For achieving data safety in IoT attribute-based encryption is one of the best ways. In this encryption method, all the access granted data users are provided a special key or password depending upon their attribute to get access to the data sea of that network The current study is focusing on the advanced encryption system with an attribute-based encryption approach to secure the IoT network.
Keywords—Access control, Attribute-Based Encryption, attribute-based access control , Internet of Things, security.
Introduction
Background
Internet has made a revolutionary progress in today’s world. With the advancement of internet, there has been a development of billions of physical devices which collects and shares data via internet. Internet of Things (IoT) refers to devices connected to internet and can also communicate independently with the network. Smart watch, smart thermostat, smart lightbulb, smart TV, smart grid, smart traffic control, smart home camera etc are common examples of IoT.
IoT has provided several benefits to individual and businesses and has simplified our way of living. However, these benefits have led to increased privacy and security challenges. Research says that the increase in IoT market has upsurged the number of data breaches since 2015. In USA, increased to 60%[1]. Another survey conducted in developed countries says that 63% of IoT owners find the device security creepy[2].
Most of the IoT devices have their own data storage facility. However, cloud can be used as a storage of data mainly in health sector. Cloud computing technology has made a revolutionary change in the field of technology. User can get access to the data from any part of the world. However, unsecured data on cloud servers can lead to serious security issues. It is essential to follow best security measures to protect data Confidentiality, Integrity and Availability[3].
Access control is the first thing when it comes to the security. Access is granted based on the attribute of the user. Various encryption method is used to secure the data on the server. The process of data encryption is the method to encode a message so that it can only be understood by the persons who know that specific method to decrypt the message. In traditional encryption schemes, flexibility and separate access control required for various application was the major issue [4]. In this modern age of overflow of information, data encryption is used to keep the respective data safe that may surface through any network structure [5]. Because encrypted data needs a special type of key or password to decrypt that specific encrypted data. For this cause in the complex and comprehensive type of network such as IoT network, the use of data encryption is much needed [6]. In this case, data is also encrypted to control access to that very data through the IoT network devices. IoT is a concept build up with the help of technology that connects the smart device in a network to provide an integrated network of access to use various software and apps by switching off and on the internet. It also helps the human being to organize all the smart devices of home or workplace to work in synchronized order making living better [7]. Its capability is also used to secure access to any network by the unique access control system features through a separately assigned IP address. For this specific feature, it is used in the digital locking systems, card reader machines so that wrong entry can be detected and blocked through the access control feature.
So to control the unique system and secure the data that flows through this network infrastructure the whole data flow should be encrypted in such a way that the data become automatically secured and fine-grained to secure the proper use by the data user [8]. For achieving data safety in a complex network structure like IoT attribute-based encryption is one of the best ways. In this encryption method, all the access granted data users are provided a special key or password depending upon their attribute to get access to the data sea of that very network. In this type of system, only after matching the access key with the proper attribute of the encryption, the ciphertext data can be decrypted [9]. So, for this reason the implication of attribute-based encryption to secure and control access to any IoT network should be investigated thoroughly.
The current research on encryption and attribute-based access control in IoT network has been conducted in a secondary qualitative approach. The relevant data has been collected from the Google scholar and library data base of Charles Darwin University. Research has shown that Blockchain technology has a great scope to solve problems of data tempering and single-point failure. So, to control this unique system and secure the data that flows through this network infrastructure, the whole data flow should be encrypted in such a way that the data become automatically secured and fine-grained to secure the proper use by the data user. For achieving the data safety in a complex network structure like IoT attribute-based encryption is one of the best ways. In this encryption method, all the access granted data users are provided with a special key or password depending upon their attribute to get access to the data sea of that very network. In this type of system, only after matching the access key with the proper attribute of the encryption the ciphertext data can be decrypted. So, for this reason, the implication of attribute-based encryption to secure and control access to any IoT network should be investigated thoroughly.
Research Goal
- The current research is focusing on the advanced encryption system, where it has been expressed how an attribute-based encryption system secures IoT network devices.
- Nowadays, IoT or the Internet of things is highly potential to reduce the gaps between the real world and virtual world. The sensors have been installed in the IoT in the real world for measuring real-world physical phenomena [10].
- The main goal is to provide an attribute-based access control to handle the security issues in IoT devices.
- The present research has analyzed the importance of the ABE or attribute-based encryption to protect the privacy of the users. It does not need to build group keys and reduces the size of the cipher text by encrypting data efficiency. It has provided a cost-effective solution to reduce the violations in IoT devices.
- The attribute-based encryption or ABE helps to encrypt the document for the users by using an attribute set directly with some attributes. In this case, an attributer set has been chosen to encrypt a message.
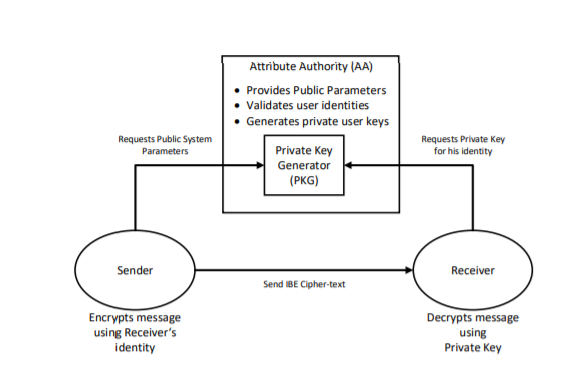
Fig 1: Participants in an Identity-Based Encryption System[10]
Research Scope
New opportunities are introduced with smart connected devices for enabling new services and merging new technologies with modern life. The users can join the network through any devices and data can be accessed from any endpoints as the devices are individually accessible. The current study describes the encryption and attribute-based access control in IoT devices. However, there is a huge possibility of malware attacks, hacking and violation of privacy[11]. With the development of new technologies, privacy issues have also become very complicated.
Therefore, unauthorized access should be evaluated properly and for this, encryption and attribute-based access control technologies are important to identify the security and privacy risks in IoT devices. In this case data is also encrypted to control access to that very data through the IoT network devices. It also helps the human being to organize all the smart devices of home or workplace to work in synchronized order making the living better. Its capability is also used to secure access to any network by the unique access control system features through a separately assigned IP address. For this specific feature, it is used in the digital locking systems, card reader machines so that wrong entry can be detected and blocked through the access control feature [12]. For the solution to this novel problem, the attribute-based control system is needed for the smooth application of IoT.
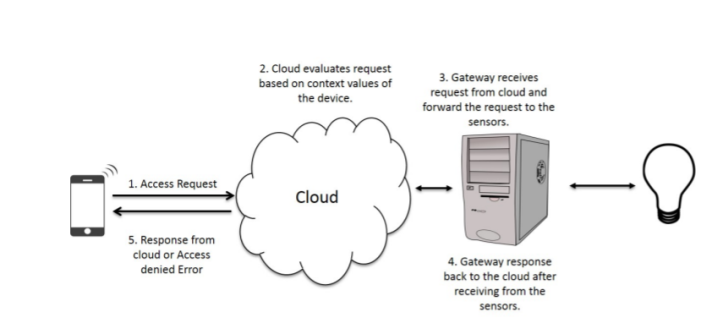
Fig 2: Lightweight in Attribute-Based Access Control System in IoT Environment [11]
Research questions
- What are the security issues found in IoT device?
- What is the role of encryption and attribute-based access control to prevent the security issues in IoT devices?
Boundaries
However, there are several challenges and boundaries in the IoT environment. The most important issue in the IoT networking system is the loss of privacy. Sometimes, the users are unaware of the protection mechanisms and security vulnerabilities of the IoT network. It causes the loss of private and sensitive information from the IoT networks. Additionally, there is a high change of flooding attacks in the home IoT networks [13]. The presence of malicious code in IoT devices is also a challenge in IoT devices, for this, access control should be required for ensuring that the third-party applications cannot violate the control boundaries.
Problem
Hence, the main problem IoT device face is their security and vulnerability issues. With the development of technologies, security issues and challenges have also risen. A vulnerability in the security camera of a particular model has been found in 2016. It is just an example of poor security system in IoT devices. Another problem is the lack of compliance with IoT manufacturing. Some examples of security risks in IoT devices from the part of manufacturers are hardware issues, insecure data storage, and transfer, lack of secure update mechanism, etc. [14]. Another security issue can be found in the insecure firmware or software. There is also a possibility of botnet attacks in a single IoT device All these problems can be seen in the IoT devices and this problem can be solved with encryption and attribute-based access control system.
Purpose statement
So, the increasing risks and security issues in IoT devices should be reduced with an attribute-based encryption method. The current research focuses on the implementation of encryption and attribute-based access control to secure the data in IoT networking system.
Aim of Research and discussion
In this specific research, the aim is to find the proper encryption method to secure the data of any IoT network and give the system user a better experience of working. From the various encryption methods, the attribute-based encryption (ABE) is one of the industry’s nest data encryption methods. The work to be done here is to examine the degree of application of the ABE to the IoT network [15]. The IoT network enables the various devices to work in an integrated network to incorporate different facilities of the various devices attached[16]. In[17], the application of IoT in creating smart homes or the internet driven locking system or reading information of chip inserted card has been thoroughly investigated to find out the data protection that has been given by the chosen encryption system. That means it will be researched that though the networking system being very much complex and elaborated if it is feasible to protect the network being hacked and its stored and surfacing data in it from being stolen, exploited, deleted, or corrupted [18]. In [19] , it is also aimed to examine the capacity of the encryption key being useful to decrypt the encrypted data as per the individual attribute. This can be found by examining the type of fine-grained single point entry access control in the pre said attribute-based encryption.
Research Hypothesis
Therefore, two possible hypotheses can be developed to continue with the research.
H1: the encryption and attribute-based access control system is useful to control the security vulnerabilities and challenges in IoT devices.
H2: the ABE or attribute-based access control system cannot reduce the issues of privacy loss and hack in IoT devices.
Structure of Paper
The current paper is divided into several parts:
- The main study paper consisting of research, abstract, background, aim and discussion, main research approach and methodology, analysis and discussion of result, conclusion, and future work.
- In the appendices section, appendix A is consisting of the literature review on encryption and attribute-based access control in IoT.
- Appendix B is related to the data sources and size.
- Appendix C contains a figure relevant to the current study.
Approach and Methodology [800]
The conduction of the research on the topic of Encryption in IoT devices will be done by the primary type of research process through the physical conduction of experiments. For the experiment setup, ESP 32 board [20] is used as an IoT platform which is low in cost, high availability and has maximum inbuilt features. For power consumption, microprocessor is used. The board consists of inbuilt static RAM, programmable ROM, WIFI and Bluetooth. To perform cryptographic operations, inbuilt cryptographic hardware is used. Free RTOS is used for memory management. In the experiment setup three libraries for Linux OS namely LIBCELIA, LIBBSWABE Library BSW, KPABE-YCT14 YCT scheme. Use of WOLFSSL library of free RTOS is used to embed the code. However, free RTOS does not support open SSL.
The experiment is done to analyse the feasibility of ESP32 board for it reliability in encrypting data using attribute based algorithm. The experiment used ESP32-S board to accomplish the experiment with the detailed port data and labels as shown below:
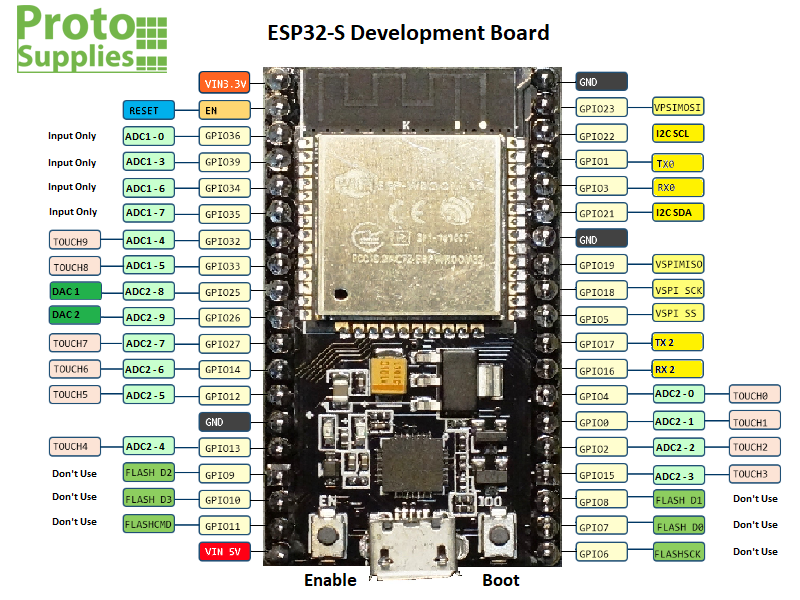
Fig 3: ESP32-S development board [20]
3 simple programmes are used as main body, one per library, were written to conduct a sequential system of operations to gauge the feasibility of the 3 proposed ABE methods on RE-Mote and ESP32. In accordance to the preliminary Setup procedure, which creates a “master key” and an “encryption key”, the software uses the algorithm to build the KeyGen, to generate a decryption key. The programme then generates a randomized string of 4-byte size that simulates the message to be sent. Following the task performed, the software will encrypt the message before decrypting it. The software sends a message across the series connection for each operation. This makes it possible to calculate the amount of time it takes to complete each operation. A high accuracy USB power metre is used to measure the energy usage. We utilized the AVHzY USB Power Meter Tester8, which permits measurements with a precision of 1015 mWh and facilitates automated data gathering from a connected PC. We were able to determine the energy spent for each operation by comparing the logs extracted from the motherboard with the access of data from power meters.
The following measures were used to assess the three ABE schemes:
- Encoding/decoding time (s), which is the amount of time it takes to run a cryptographic algorithm.
- Energy consumption for Encoding/decoding (mWh), which is the total amount of energy used by the board to perform a Cryptographic algorithm.
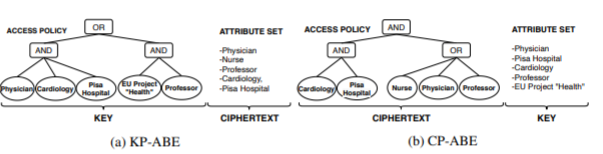
Fig 4: KP-ABE (a) and CP-ABE (b)- Schematic examples [21]
Encryption has been explored for a growing number of characteristics, ranging from 5 to 50. For the scheme of CP-ABE (BSW series), which denotes the number of leaves in the policy tree, whereas for KP-ABE enabled schemes, it indicates the set’s size of attributes (GPSW and YCT). Since the branches of a policy tree reflect the technicality of arguments of both the policies, while the attribute group characterizes the real justifications utilised to assess a policy, these two components may not have the same meaning. They both, nevertheless, provide a way to measure the reliability of a software’s rules for access control. Ten independent copies of the experiment have now been carried out for each test condition. The approximate amount of the measurements, and also the 95 % confidence band, are reported in our findings. It’s worth noting that now the number of duplicates and setups examined in our studies is restricted in terms of attribute values. This would be attributable to the fact that some phases in the experiment execution can indeed be automated, resulting in a significant increase in the time necessary to complete them. Owing to the modest variance of the results, 10 replicates should be sufficient to provide statistically acceptable averages. The frequency of processes performed by the Decryption algorithms increases in a linear association with the frequency of examined leaves and intermediate nodes (including roots). The above indicates that policies have the same amount of leaves but a differing “shape” might have different outcomes. We created flat access policies with a solitary internal node (the roots) linked to an AND operator and numerous child nodes, one per attribute. The worst case scenario for decrypt algorithms involves flat policies. However, the Decrypt algorithm is obliged to examine all of the policy tree’s leaves with a flat policy, as well as the leaf visit is usually the heftiest investment in decryption.

Fig 5: Flat and 3 level policy example diagram [22]
Innately, findings obtained employing 3-level and flat policies overestimate ABE bandwidth utilization, because all the types of policies are, by its description, are the worst-case situations for decryptions. In the actual world, nevertheless, the policies in question should be much more varied, since they represent the complexities of a person’s right of access to information as in Key-policy attribute-based encryption (KP-ABE), or as it is being explained as the broad range of units that can have access to singular bit of data as in the Cipher text-Policy Attribute-Based Encryption (CP-ABE). The building access rules with OR gates provide this diversity and flexibility. Such gates greatly reduce the quantity of leaves and nodes that must be assessed in order to meet a policy, saving time, energy and essential resources for the sensors. Now we’ll look at the underlying notion behind an average-case event which enables us to more properly predict decryption performance. The average-case performance can be determined by creating a large number of access policy/attribute set pairs at random, confirming that the produced attribute set meets the generated policy for each couple, and then executing a decryption cryptic operation on each of the pairs. We examine the decryption with overall energy and time consumption required to execute the process of decryption, just as we would in the worst-case situation, so that we can compare the findings to those obtained while using the worst-case scenario. To accomplish this, we decode many distinct attribute / access policies set pairs.
References:
[20] ESP32-S Development Board – ProtoSupplies (2021). Available at: https://protosupplies.com/product/esp32-s-development-board/ (Accessed: 28 September 2021).
[21][22] Girgenti, B., Perazzo, P., Vallati, C., Righetti, F., Dini, G. and Anastasi, G., 2019, June. On the feasibility of attribute-based encryption on constrained IoT devices for smart systems. In 2019 IEEE International Conference on Smart Computing (SMARTCOMP) (pp. 225-232). IEEE.