In your view, what is the most effective way to address the problem of terrorism?
Since the events of September 11, 2001 (hereafter referred to as 9/11) in the US, the face of terrorism has changed (Hoffman, 2002). The concept of modern terrorism was first made official in 1968 (Jenkins & Johnson, 1975). Over a period of 33 years, from 1968 until the World Trade Centre and Pentagon attacks in 2001, only 1000 Americans had been victims of international terrorism. In those agonising 90 minutes on 9/11, 3000 people were killed, making the event the most lethal terrorist attack in history. As a result, the US created the department of Homeland Security and many countries, fearing ongoing attacks from Al-Qaeda (Walter & Sandler, 2005), put internal and external measures in place to prevent terrorist attacks. However, there are arguments that the 9/11 attacks could have been avoided. Certainly, taking into consideration the tragic loss of life, lessons can be learned for future counterterrorism efforts (Hoffman, 2002). This essay offers effective actions that may address the problem of terrorism and how lessons from 9/11 and other attacks support these viewpoints.
Flexibility
In Hoffman’s (2002) view, one of the key errors made by the United States in not preventing the 9/11 attacks was underestimating the capabilities of terrorists. Americans believed that such devastating actions were beyond the capabilities of terrorists and that terrorists could not organise mass, simultaneous aviation-focused attacks such those in New York and Washington in 2001. The fact that the terrorist group(s) were able to cause so much damage to US citizens can be considered to be a result of the US defence’s inability to estimate the extent to which Islamist terrorists would go to make themselves heard (Davis & Jenkins, 2002). Clear evidence of this error was that, as a result of the 9/11 attacks, the US Government immediately put measures into place that covered airports and other public transport. This was a reactive measure to prevent further events like the one in 2001. These defensive measures show that the US now fears terrorist groups’ abilities to execute similar attacks with the resultant large numbers of casualties. However, defending areas that have already been targeted by Islamic terrorists in 9/11 cannot be claimed to be an efficient counterterrorism method, as terrorists will find new targets to attack. Thus, the first and most important point in adopting effective methods in combating terrorism is flexibility.
Hoffman (2002), while criticising the US’s underestimation of Al Qaeda’s power, discusses this solution, claiming that the US needs a system that allows for counterterrorism to be operational across a broad technological spectrum. Nothing can be deemed to be optional and it must be
accepted that terrorist groups have an operational basis that allows them to attack on a large scale. This proposition contrasts with the operations of the US Department of Homeland Security that invests nearly $100bn annually on identifying trends in terrorist attacks, a tactic that, because of 9/11, has been proved to be erroneous (US Department of Homeland Security, 2014). Granted, it would be unrealistic and would also be time-consuming and expensive to adopt an all-encompassing paranoiac attitude to matters of security, as this would create havoc in the countries which feel in danger of being targeted by terrorist groups. However, the time and resources spent on researching trends can be invested in other forms of intelligence defence mechanisms and strategies (explained later in the essay), as generalising was proven irrelevant by the 9/11 events. For instance, Brian Jenkins (1975) claimed that terrorists considered the number of victims to be less important than the number of people who heard about the terrorist acts. This claim was believed to be true until two-and-a-half decades later, when 9/11 claimed 3000 victims in 90 minutes.
Profiling of leaders
Another error that can be discerned in the terrorism research prior to 9/11 is the fact that the person who was later called the CEO of terrorism, Osama bin Laden, was given little attention before the event. His CV, which was on the desks of America’s intelligence offices and had the most important information, was overlooked. It could be argued that if more attention had been paid to it, the US would have been able to defend its citizens more effectively. Bin Laden was educated at a top university in the Kingdom of Saudi Arabia, graduating with a degree in Business Administration and Management. He was adept at technology and was a modern leader who could have organised an event in any geographical area by using technology (Scheuer, 2011). This is further evidence of how the US underestimated its enemy’s capabilities prior to the 9/11 events. The fact that the country (and, equally, other nations) is now constantly on the alert and airports have taken additional security precautions, deemed to be necessary to prevent another similar event, means that there is hope that the Department of Homeland Security now has a good understanding of the profiles of current leaders of Al-Qaeda and other terrorist networks.
For most of the time, as was the case with bin Laden, terrorist leaders do not hide away in the shadow until after a great attack for which they claim responsibility. On a regular basis, these leaders thrive on attention and will therefore threaten the American nation, the Western world and their Muslim enemies (or the infidels, like the Kingdom of Saudi Arabia or Egypt). They will take actions to reaffirm their right to lead which will often involve small scale-terrorist attacks (Davis & Jenkins, 2002). Most of the time, these are sufficient to allow intelligence officers to build a comprehensive profile of the terrorist leaders of the 21st century.
New recruits
Another technique that would aid the counterterrorism strategy would be to pay more attention to the internal affairs of countries within which terrorists are recruited. Pillar (2004) maintains that one of the roots of terrorists’ extremist behaviour are ‘closed economic and political systems in much of the Muslim world that deny many young adults the opportunity to build better lives for themselves’ (Pillar, 2004, p. 101). The lack of opportunities for young adults to access education that would help them to advance on a career path in Islamic countries allows terrorist groups to recruit these individuals (Katzman, 2005). More often than not, newcomers, lacking a future that education could offer, feel a sense of belonging as a member of a group that has set rules, a purpose and targets when they are offered training (Krueger & Maleckova, 2003). Ultimately, belonging to a terrorist group becomes a way of life and has its own cycle, as demonstrated in Figure 1, below. A key implication of the lifecycle that new recruits experience is an understanding that terrorist attacks (particularly suicide bombing, which is considered a high risk form of attack) can be prevented at its inception stage.
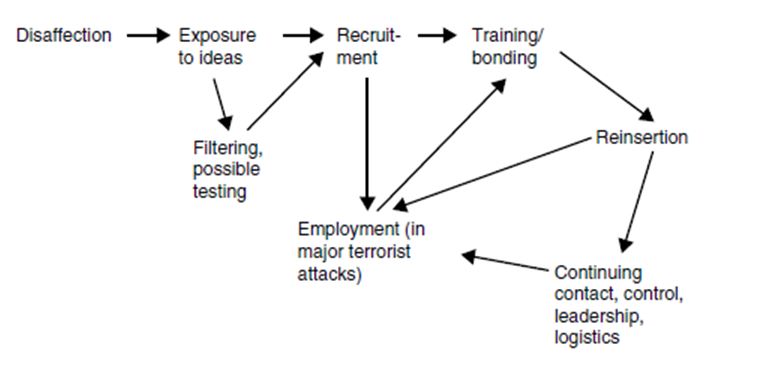
Figure 1. Lifecycle of new terrorist recruits. From Davis & Jenkins, 2002, p. 19
In addition to Pillar’s (2004) findings regarding the lack of alternatives for young people, an issue that seems to be overlooked is the power of the extremist groups to suppress any resistance of citizens who have anti-terrorism views in the countries where terrorism is widespread (Hoffman, Inside terrorism, 2013). Most Al Qaeda members are trained not to hold back from protecting the interests of the organisation and attaining the purposes set by their leaders, even if this means sacrificing their own lives (Volkan & Sinclair, 1997). Therefore citizens who disagree with the terrorist movements or who are perceived to be a threat will be attacked with uncanny violence, if the situation requires it. Moreover, terrorist attacks, particularly of the magnitude of 9/11, can be seen to be a way for Islamist terrorists to expand their existing network. Many Islamic countries perceive the US to be an enemy and success against Western leaders would demonstrate their true power (Stern, 2003).
Deterrent vs. pre-emptive approach
Counterterrorist actions have been classified by researchers (e.g. Arce and Sandler, 2005) into two categories: deterrent and pre-emptive. The first category includes all precautionary measures taken at airports or the use of metal detectors in public institutions, while the second category encompasses attacks on perceived sponsor states, bombing training camps of terrorist groups, etc. There have been numerous debates (Sandler, 2005; Faria, 2006; Sandler & Siqueira, 2006) regarding the effectiveness, repercussions and economic aspects to determine which type of action should be employed in the fight against terrorism. It is my opinion that it is unrealistic to analyse which category would benefit victims of terrorism more, as the reality is that both defence mechanisms are necessary and depend on the action of terrorists. Pre-emptive tactics employed by the US, as in the case of military action taken in Afghanistan, had negative repercussions. There was an increase in recruiting new terrorists in the targeted country that, in turn, has led to suicide attacks. These have necessitated deterrent actions on American soil when new attacks have taken place. This vicious cycle requires counterterrorist operations to make use of both deterrent and pre-emptive tactics.
The defeat of the Soviet Union was a sign that any external power could be defeated with the help of Allah, according to bin Laden, in one of his speeches (Miller, 2001). Bin Laden’s speech did not take into account all the factors that determined the end of the Soviet Union as an entity and
credited the withdrawal of the Soviet Union from Afghanistan entirely to the Taliban’s efforts against the invader. The former Al Qaeda leader made similar claims regarding the US, expressing his desire to neutralise America’s power through repetitive attacks that would bring the economy and the military resistance of the US to its knees (Davis & Jenkins, 2002). Deterring terrorist attacks is highly dependent on convincing Al Qaeda and similar organisations that the idea of defeating the American nation is unrealistic. However, to assume that any tactic, whether pre-emptive or deterrent would stigmatise terrorism and guarantee its demise is ‘both ahistorical and naive’ (Davis & Jenkins, 2002, p. 4).
Terrorism is, ultimately, difficult to combat because those relying on it have no alternative tactics to make themselves heard and, more often than not, have nothing to lose. This is a core reason why any small or big victory against terrorist groups cannot be assumed to be a successful step towards eliminating this danger for America and the EU. Although the death of bin Laden was an important stage in the effort to defeat terrorists, this should not be celebrated as the end of Al Qaeda, which has survived beyond the death of its leader (Jongman, 2005).
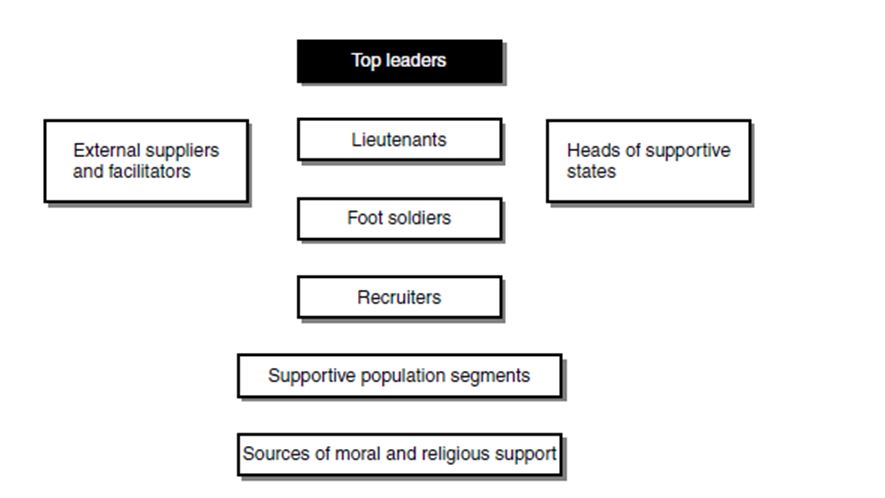
Figure 2. The matrix of actors involved in a terrorist system. Adapted from Davis & Jenkins, 2002, p. 15
Therefore they would respond differently to threats. If the US were to dismantle the economic backing that Al Qaeda and other terrorist groups use to survive, it could succeed in reducing the ability of terrorist groups to organise attacks and attract new recruits − a solution offered by the late bin Laden himself. In an interview in December 2001, bin Laden declared that he intended attacking the economy of the US as he believed that this would lead to the nation’s end. America would be incapable of funding its military power anymore (Davis &Jenkins, 2002). As a pre-emptive measure, bin Laden’s theory could, in fact work very well for the American and European anti-terrorist movements, as they could locate and threaten the external suppliers through use of intelligence and surveillance equipment.
Immigration policies
Apart from deterrent actions against external attacks, the internal policies of the US and the EU also reconsidered immigration policies, targeting citizens from countries like Afghanistan and Iraq where terrorist groups have training camps. This has sparked a debate around racial profiling and racism against Muslim countries and their citizens, as scrutiny of these individuals has heightened since 9/11 (Turnlin, 2004). Even though it can be claimed that some of the internal policies regarding immigration of citizens from Arab countries unrightfully discriminate against some citizens who may have no terrorist intent by subjecting them to increased security measures, it must be understood, at an international level, that all these measures are intended to protect all citizens from violent attacks.
However, it is not guaranteed that this measure will eliminate attacks, as there have been cases of American or British citizens, for instance, who have aligned themselves with Al Qaeda and other terrorist movements subsequent to the 9/11 events. This seems to confirm a notion, widely circulated in the academic world that, since 9/11, Al Qaeda, has gained in status amongst existing and upcoming terrorists. Hoffman (2013) claims that the constant presence of the group in the Western media has given this terrorist group an exposure otherwise unattainable. This, it could be argued, has always been a core purpose of bin Laden and other Islamic war leaders. Therefore, without realising it, the media has kept all believers in the jihad up to date with the unfolding of the events.
Technological advances are another example of tools developed by the Western societies that terrorist groups can make use of. At the same time, because all digital information sent out can be tracked, frequently intelligence groups have intercepted messages between leaders and actors regarding upcoming attacks (Kelley, 2001). When considering 9/11, it is apparent that without technology, bin Laden would have not been able to broadcast his message so widely. Nevertheless, as Hoffman (2002) argued at the beginning of this essay, America failed to make use of the information that bin Laden himself had delivered to them. Although America had been warned, it underestimated Al Qaeda’s ability to wreak such havoc.
Conclusion
In summary, a counterterrorism strategy should be flexible, make use of both deterrent and pre-emptive measures, gain an insight into the ongoing co-opting of new members into terrorist groups and target sponsors of these organisations. The fluidity of the terrorist groups makes it difficult for the US and the EU to determine the trends of these groups in terms of planned attacks and existing members. Therefore, the attacks on training camps should be considered as interim successes and should not be generalised as being destructive to the groups. In a nutshell, terrorist groups should not be underestimated; as was the case prior to the 9/11 events and the intelligence groups should focus on identifying economic aspects that the terrorist organisations make use of, in order to tackle the military terrorist actions.
An additional suggestion that was not explored fully in this essay is that leaders of countries where terrorist groups operate from should be offered positive incentives in order to cooperate against terrorism. Although this has not proved to be successful in every instance, (for instance the E3 (UK, France and Germany) group’s offer to Iran of trade benefits in exchange for the country’s commitment to abandon the development of nuclear weapons) this tactic cannot be deemed to be ineffective in every instance (Davis & Jenkins, 2002). Partnerships with Arab countries would help eliminate the stigma in European and American countries towards Arab countries and the people in these countries.
Bibliography
Davis, P. & Jenkins, B. M. (2002). Deterrence and Influence in Counterterrorism: A Component in the War on al Qaeda. Rand Corporation.
Faria, J. (2006). Terrorist innovations and anti-terrorist policies. Terrorism and Political Violence, 47-56.
Hoffman, B. (2002). Rethinking Terrorism and Counterterrorism since 9/11. Studies in Conflict & Terrorism, 303-316.
Hoffman, B. (2013). Inside terrorism. Columbia University Press.
Jenkins, B. M. & Johnson, J. (1975). International Terrorism: A Chronology, 1968-1974. Santa Monica: Rand.
Jongman, A. J. (2005). Political terrorism: A new guide to actors, authors, concepts, data bases, theories, and literature. Transaction Publishers.
Katzman, K. (2005). Al Qaeda: Profile and Threat Assessment. Congressional Research Service Reports on Terrorism.
Kelley, Jack. “Terror groups hide behind Web encryption.” USA today 5 (2001).
Krueger, A. B. & Maleckova, J. (2003). Education, poverty and terrorism: Is there a causal connection? The Journal of Economic Perspectives , 119-144.
Miller, J. (2001, September 13). Hunting for bin Laden. Retrieved March 2, 2014, from Frontline: http://www.pbs.org/wgbh/pages/frontline/shows/
Pillar, P. R. (2004). Counterterrorism after al Qaeda. Washington Quarterly, 101-113.
Sandler, T. (2005). Counterterrorism – A Game-Theoretic Analysis. Journal of conflict resolution, 183-200.
Sandler, T. & Siqueira, K. (2006). Global terrorism: deterrence versus preemption. Canadian Journal of Economics/Revue Canadienne d’économique , 1370-1387.
Scheuer, M. (2011). Osama Bin Laden. Oxford University Press.
Stern, Jessica. “The protean enemy.” Foreign Affairs (2003): 27-40.
Turnlin, Karen C. “Suspect First: How Terrorism Policy Is Reshaping Immigration Policy.” California Law Review 92.4 (2004).
U.S. Department of Homeland Security. (2014). Budget-in-Brief Fiscal Year 2014. U.S. Department of Homeland Security.
Volkan, V., & Sinclair, C. (1997). Bloodlines: From ethnic pride to ethnic terrorism. New York: Farrar, Straus and Giroux.
Walter, E. & Sandler, T. (2005). After 9/11 is it all different now? Journal of Conflict Resolution, 259-277.